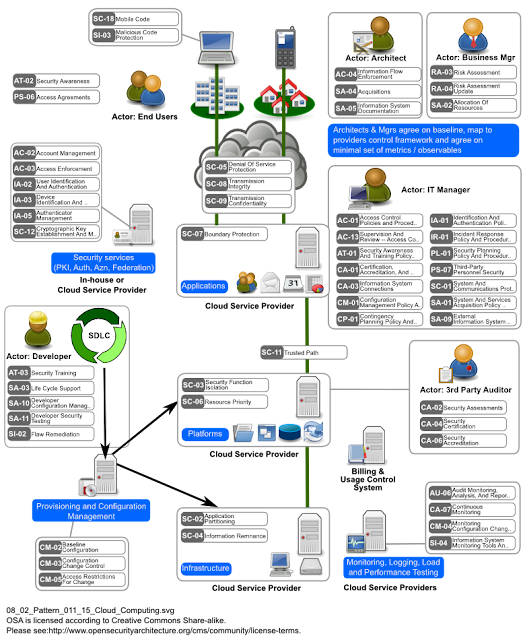
 |
| Cloud Computing Security Pattern |
Legend:
Services provided by the Cloud Computing environment are not under direct control and therefore a few control families become more significant. Controls in the CA series increase in importance to ensure oversight and assurance given that the operations are being "outsourced" to another provider. SA-1/4/5 are crucial to ensure that acquisition of services are managed correctly. CP-1 helps ensure a clear understanding of how to respond in the event of interruptions to service delivery. The RA controls are very important to understand the risks associated with the service in a business context, but may be challenging to implement, depending on the supplier and the degree of visibility into their operations.
Description:
Cloud computing can be defined as the provision of computing services via the Internet such as
- Applications (Software as a Service or SaaS),
- Platforms,
- Infrastructure (IaaS),
- Process Orchestration and Integration.
The cloud model is of great interest to service providers because it likely represents the next great wave of innovation sweeping across the the Internet and presents tremendous business opportunities for those who can successfully define and implement the new paradigm. End users are interested because services are reasonably priced and can be accessed from any browser giving access to the computing environment from any location and making collaboration much easier. Corporate IT departments are interested because the model reduces capital investments, removes constraints on power and space, may deliver much faster development and implementation times, and promises to simplify the management of complex environments.
So it should be a simple decision to scrap the legacy environments and move to the cloud? Well, for many use cases especially private end users and Small to Medium Enterprises (SME's) the risk versus reward is strongly in favor of adopting relevant new Cloud services as they become available. However for large organizations, especially those in regulated sectors the decision is not so simple.
Key control areas:
There are a number of control areas that must be consider carefully before you move computing operations to Cloud Services:- Contractual agreements- who owns the data, what rights or recourse do you have for security breaches or incidents, what happens when you want to move to another provider?
- Certification and 3rd party audits- is the provider certified e.g. SAS-70 (remember the scope of a SAS-70 will determine how much trust you can place in it), can you request independent audits of the facilities and operations?
- Compliance requirements- do they meet your organisations compliance needs, e.g. Data Privacy, Safe Harbor. Where are the operations located and where would your data reside? Be aware that providers will need to obey law enforcement regulations in their operating locations, and may be obliged to disclose data without your consent to government and law enforcement agencies if requested.
- Availability, reliability and resilience- what happens when the service is not available? What are the points where you need additional resilience for access?
- Backup and recovery- in the event of a physical or logical disaster what are the Recovery Point and Recovery Time Objectives (RPO/RTO) that you will need and they will provide?
- Service levels and Performance- what do they offer and what do you need? What happens if the service is below expectations? Remember a service may be available but have an unacceptable performance level or response times.
- Decommissioning- will data be securely deleted once it is no longer needed? What about the virtual machines or processes you are using? Will fragments reside client side in your browser that you need to be aware of?
A key activity that is shared by the architect, the security manager and the business manager is to jointly agree the controls required. They should:
- Agree on the control baseline applicable to this cloud sourcing activity/service
- Confirm how this translates into the control framework of the cloud provider, because unlike regular supplier contracting it is very improbable that the cloud provider will directly implement the controls specified by the customer. It is more likely that the cloud service provider will refer to his standard (PCI DSS adherent, NIST adherent or ISO adherent) control framework.
- Decide on additional risk mitigating controls.
You will likely need supporting services if your process is comprised of a number of cloud services. Some of the important ones to consider are:
- Security (OpenID, .Net Access Control, PKI), Billing (DevPay),
- Load Monitoring and Testing (Soasta, Hyperic)
- Provisioning and Configuration Mgmt (Rightscale)
This is an evolving area and standards for integration are still emerging. Maintaining a security context across a number of seperate cloud providers can be a real challenge! Especially when you consider that you likely want to use roles to manage authorisation to different functions. There is a good case for maintaining your own directory and federation services that you will use to provide authentication across in-house and cloud services. Where possible it is recommended to abstract the authentication and authorisation services behind industry standard interfaces such as SAML
Cloud services will likely be complex webs and in fact the service you recieve may in fact be provided by another cloud provider (e.g. Box.net use Amazon S3). This became apparent when an Amazon S3 outage affected a number of services that had been built using Amazon for storage. The chain of dependencies may not be obvious, make checks according to the criticality of your requirements. If creating custom code elements the developer constantly needs to consider code refactoring to keep the code base as simple as possible and hence mitigate what is frequently the biggest overall IT Risk, complexity.
Examples:
Applications/SaaS include
- SaaS: Salesforce, Google Docs, Facebook, LinkedIn, Doodle.
Platform service providers include
- Content: SpringCM, Xythos OnDemand, GoogleBase
- Platform as a Service: Force.com, Google App Engine, Bungee Labs Connect, Etelos, Intiuit Quickbase, LongJump, Apprenda SaasGrid, Oracle Saas Platform, MS Azure
- Data: Amazon S3, Box.net, Google Base, Amazon SimpleDB, Trackvia, Microsoft SSDS.
Infrastructure as a service include
- Cloud Providers : IBM Blue Cloud, Joyent, GoGrid, SunGrid, Amazon EC2,
Examples of Integration and Orchestration include
- Integration: Boomi, Mule OnDemand, OpSource Connect (OSB), Amazon SQS, Microsoft BizTalk Services
- Orchestration: ProcessMaker, Appian Anywhere, Skemma, Intensil
- Billing, Contract Management: OpSource/LeCayla, Aria, eVapt, Amazon DevPay, Zuora
- Security: OpenID, OAuth, Ping Identity
- Cloud Deployment: rPath, CohesiveFT, VMWare, Xen, Parallels, Bea Weblogic Server VE, 3Tera AppLogic, Elastra Cloud Server
Assumptions: Cloud computing is an evolving area and it is expected that this pattern will be revised within a year to reflect developments. It is likely that for large corporates a prudent and realistic strategy will be to deploy for test and development environments, which give some benefits without the downside of exposing production data sets.
Typical challenges: Trustworthiness of partner-how to establish and track? Lack of certainty on many aspects of controls required. Compliance. Ability to move to other providers. Authentication and authorization across multiple providers and systems.
Indications: Organization who will provide some or all of their computing environment via cloud services. Organization has constraints on existing power or space, desire to reduce capital expenditure, need to provision services rapidly, big variations in computing demand, collaboration with wide range of B2B partners.
Contra-indications: Lack of understanding of your compliance needs or inability to confirm how the supplier will meet your requirements.
Resistance against threats: Untrustworthy supplier, eavesdropping, impersonation, data theft, lack of performance and logical and physical disasters are addressed by this pattern. Consider checking supplier applications for Cross-site scripting (XSS) attacks which can be used to log keystrokes and capture data, and propagate web application worms such as Samy. Feed injection for RSS and Atom can allow an attacker to compromise applications, if feeds are not properly secured.
All other major vendors have their own literature and approaches, just search on Google!
This is very useful information. Thanks for sharing
ReplyDeletecloud computing course in Chennai
Data safety is obviously an issue of top crisis at the moment. It's the purpose behind the institution of numerous institutes providing classes on information security courses.
ReplyDeleteThanks for sharing...!!!
Hello, I truly like to reading your post. Thank you so much for taking the time to share such a nice information. I'll definitely add this great post in my article section.
ReplyDeleteData security service
We are the best IT training and placement institute in Chennai with training center in Velachery & T Nagar. Join us for IT training and placement Salesforce Training in Chennai
ReplyDeleteGood Post! Thank you so much for sharing this pretty post, it was so good to read and useful to improve my knowledge as
ReplyDeleteSplitwise
appvn
Thanks for sharing your ideas and view, this is appreciable.
ReplyDeleteUK VPS Hosting
Very informatine. Thanks for sharing. SAP Cloud Computing Recruiters | <a href="https://www.xforia.com/working-from-home-and-staying-motivated/>Creative staffing services and solutions Texas</a>
ReplyDeleteVery impressive. Thanks for sharing. SAP Cloud Computing Recruiters | Creative staffing services and solutions Texas
ReplyDeleteCloud services should prove maximum security for breaches and all these kind of issues.
ReplyDeleteWebsite Development Melbourne
Custom website development Melbourne
Wordpress website development Melbourne
Standard visits recorded here are the simplest strategy to value your vitality, which is the reason why I am heading off to the site regularly, looking for new, fascinating information. Many, bless your heart!
ReplyDelete360DgiTMG data analytics course malaysia
Set aside my effort to peruse all the remarks, however I truly delighted in the article. It's consistently pleasant when you can not exclusively be educated, yet in addition, engaged!pmp certification in malaysia
ReplyDeleteinformative blog...!
ReplyDeleteartificial intelligence course in delhi
stunning, incredible, I was thinking about how to fix skin inflammation normally.I've bookmark your site and furthermore include rss. keep us refreshed.
ReplyDeletehttps://360digitmg.com/course/project-management-professional-pmp
This is a great post I saw thanks to sharing. I really want to hope that you will continue to share great posts in the future.
ReplyDeletewhat is hrdf
this is a very nice article. IT Technology consulting firm texas | SAP Cloud Computing Solutions Texas
ReplyDeleteI looked at some very important and to maintain the length of the strength you are looking for on your website
ReplyDelete"
hrdf claimable courses"
Thanks for sharing amazing information. We are one of the leading Website Development Company in Chennai and providing services like Digital Marketing Services , Ecommerce Services in Chennai, ERP Services, CRM Services in Chennai, and more.
ReplyDeleteI have a strategic I'm seconds ago chipping away at, and I have been at the post for such data
ReplyDeleteHRDF training
I truly like your style of blogging. I added it to my preferred's blog webpage list and will return soon…
ReplyDeletemasters in data science
You know your projects stand out of the herd. There is something special about them. It seems to me all of them are really brilliant!
ReplyDeleteBest Institute for Data Science in Hyderabad
I'm cheerful I found this blog! Every now and then, understudies need to psychologically the keys of beneficial artistic articles forming. Your information about this great post can turn into a reason for such individuals.
ReplyDeletearttificial intelligence training in aurangabad
This comment has been removed by the author.
ReplyDeleteObviously, this blog is awesome. I like the given information. Keep Updating. Data safety is obviously an issue of top crisis at the moment. It's the purpose behind the institution of numerous institutes providing classes on information security courses. Webserver hosting play important role in online business. If you have interested in the best USA VPS Hosting you can ask us for more details and services.
ReplyDeleteThanks for sharing...!!!
Wow it is really wonderful and awesome thus it is very much useful for me to understand many concepts and helped me a lot. it is really explainable very well and i got more information from your blog.
ReplyDelete3D Laser Scanning Targets
3D Scanning Reverse Engineering
Reverse Engineering Services
ReplyDeleteI need to to thank you for this great read!! I definitely loved every bit of it.
CHECK NOW I have got you bookmarked to look at new stuff you .
Very useful post, i think amazing content is very Useful for any website to attract people.
ReplyDeleteWeb Hosting in UAE
Thanks For your post. This is rally helpful for Data Science for beginner.
ReplyDeletedata science courses aurangabad
This is very informative blog, writing skill is very creative.This true information about Cloud Computing Security Pattern
ReplyDelete. If you want to know about Server hosting, i can help you USA Dedicated Server.
Thanks for your blog. This is very nice article. Very Impressive. This helps me a lot. Thanks for sharing your thoughts Braided Rugs Online
ReplyDeleteThis is the best blog ever. It's helping me a lot. Thanks for this kind information. BEST EXPLANATION EVER.
ReplyDeleteRound Pouf Online
Great Blog !! Services provided by the Cloud Computing environment are not under the direct control and therefore a few control families become more significant. If you have interested in the best Canada VPS Server you can ask us for more details and services.
ReplyDeleteThanks for your interesting blog. This is a very good article. Very Impressive. This helps me a lot. Thanks for sharing your thoughts UAE VPS Server
ReplyDeleteGreat blog created by you. I read your blog, it's the best and most useful information. You have done great work. Super blogging and keep it up posting. Romania VPS Server
ReplyDeleteI always enjoy reading posts that provide knowledge-based information like this blog. Keep it up. Turkey VPS Server
ReplyDeleteYour blog is so marvelous and everything is a proper way to write I spend about the blog for the suggestions, recommendations, and solutions to Cloud Security threats and risks. I share such information, especially about France VPS Server you can ask us for more details about hosting services.
ReplyDeleteVery fascinating and awesome blog. A single attentive reading is enough to understand the points and the information mentioned. I share such information, especially about India VPS Server you can ask us for more details and services.
ReplyDeleteAmazing blog... Thank you for the very good and meaningful blog. It is very helpful for all blog writers. I share such information, especially about Ukraine VPS Server which can improve your business, I will be glad to help you.
ReplyDeleteThis comprehensive piece offers a thorough exploration of critical considerations and control areas when transitioning to cloud computing security . The delineation of key control families, such as contractual agreements, certification, compliance, availability, and security, provides valuable insights for decision-makers. The emphasis on joint agreement among architects, security managers, and business managers underscores the collaborative effort needed to establish effective controls. The inclusion of practical examples and awareness of emerging standards adds depth to the discussion, making it a valuable resource for those navigating the complexities of cloud adoption.
ReplyDelete